So, uh, there’s nothing interesting last week.
QP farming time as it’s currently half AP 😪
Dumping this here so I can refer to this when needed and in case anyone is looking for this.
function inet_prefixlen_start(string $inet, int $version, int $prefixlen): ?string
{
switch ($version) {
case 4:
if (filter_var($inet, FILTER_VALIDATE_IP, FILTER_FLAG_IPV4) !== false) {
$pack = 'c*';
$size = 8;
}
break;
case 6:
if (filter_var($inet, FILTER_VALIDATE_IP, FILTER_FLAG_IPV6) !== false) {
$pack = 'n*';
$size = 16;
}
break;
}
if (!isset($pack)) {
return null;
}
$ipArray = unpack($pack, inet_pton($inet));
$groupMask = (1 << $size) - 1;
$fullSize = $size * count($ipArray);
$groupCount = count($ipArray);
for ($i = 0; $i < $groupCount; $i++) {
$mask = $groupMask;
$indexStart = $i * $size;
for ($j = 0; $j < $size; $j++) {
$fullIndex = $indexStart + $j;
if ($fullIndex < $prefixlen) {
continue;
}
// shifting goes from the end, one less of size:
// (size 8)
// i = 0 -> shift = 7 (1000 0000)
// i = 7 -> shift = 0 (0000 0001)
$index = $size - $j - 1;
$mask ^= 1 << $index;
}
// ipArray is 1-indexed because that's how unpack works
$group = $i + 1;
$ipArray[$group] = $ipArray[$group] & $mask;
}
return inet_ntop(pack($pack, ...$ipArray));
}
/**
some sample data
['1.2.3.4', 4, 24, '1.2.3.0'],
['1.2.3.5', 4, 31, '1.2.3.4'],
['::10.0.0.3', 4, 32, null],
['1:2:3:4::', 4, 24, null],
['invalid', 4, 32, null],
['1:2:3:4::1', 6, 64, '1:2:3:4::'],
['1:2:3::1', 6, 64, '1:2:3::'],
['1:2:3:4:5:6:7:8', 6, 64, '1:2:3:4::'],
['1::4:5:6:7:8', 6, 64, '1:0:0:4::'],
['1:2:3:4::10.0.0.1', 6, 64, '1:2:3:4::'],
['1:2:3:ffff::1', 6, 56, '1:2:3:ff00::'],
['::3', 6, 127, '::2'],
['1.2.3.4', 6, 128, null],
['invalid', 6, 128, null],
*/
Or just use one of those IP handling libraries.

Apparently it’s new year.
Which means GSSR! Extra Quick! I considered Extra Buster 1 as well but in the end Koyan Dark isn’t all that important in term of support and getting Skadi Summer means I can save more SQ for whatever upcoming servants.
Unfortunately no Skadi Summer so I still have to roll for her later. I also hoped for anyone but Voyager since I’ve seen him enough times in other account but oh well. It’s kind of the worst possible outcome for me.
Better luck next GSSR, I guess.
On the other news, Kotomine-alike servant is finally implemented and… I don’t quite care about him. So that’s nice since I don’t have enough SQ for 330 rolls.
Unfortunately there’s nothing else new. There’s mention of LB7 part two coming up end of this month but nothing immediate. Let’s see if anything is announced on Wednesday.
LB7!
…and that’s it. I don’t know if there will be raid or anything around the end but for the moment I’ll just do it slowly. Also I still haven’t caught up with the story since LB4 so I’m skipping the story. It’s also rather annoying reading and fighting at the same time anyway.
On the other news, lineup for GSSR has been announced. The lineup is mildly annoying this time around. Koyanskaya of Darkness and Skadi Summer are the two main I kind of want/need but the probability at just 20% and 16.67% respectively, it’ll probably be a miss. Also Skadi Summer will most likely see revival banner mid next year so there’s that.
If I want something that’ll surely be useful I’d just pull Berserker Area. At worst I’ll get Raikou which usefulness is a bit limited. Or Assassin Single Target – MHX isn’t all that useful but I kinda like her design and the other two I already have… or so I thought. I mixed up with NA account (RIP) about owning First Assassin. I guess no Assassin ST for me since he’s not all that useful especially at NP1.
In the end I’ll probably just go with Extra Buster 1 for Koyan Dark. Even if her banner is rerun this new year I won’t have enough SQ to roll for her safely and even if I don’t get her the rest are still pretty useful even Abigail Summer if only for eyecandy. The rest I already have but NP2+ of any of them should prove useful (except for Oberon maybe).
Done with the event. I didn’t expect to need to farm specifically for box tickets especially as that’s the one I stacked the CE for the most.
As for challenge quest, I felt like testing squirtoria so I used her and she did it in three turns as expected. I think it’s easier than Orion I used last time.
With everything cleared up, I’m back to farming embers so I can get Arc to 120 as soon as possible. I really should stop doing this level 120 thing.
On gacha rolls, I ended up doing 11 rolls for Saber. I got nothing of course. I shouldn’t have done that. At least I’m not rolling for Nero Bride this time 😇 She would be kind of useful but really I need to not waste any more SQ. It’ll probably take me until anniversary next year before I roll anything.
Suddenly Christmas 2020 rerun. Well I guess it’s not quite dead weeks until LB7. I’m currently slowly farming until the final node is open. At only 20 boxes it’s not really all that useful. Being able to get 20 skill stones is still welcome but I definitely need way more than that.
On the other news, I did 6 rolls on Melusine banner and thankfully got her (to NP2). Interestingly it only took me 4 tickets on her banner last year, making it only costing me 10 rolls total to get her to NP2. This account sure is weird, when something comes up, it comes up a lot (MHXA NP4, Reines NP5, Bunnytoria NP6, Arcueid NP5); and when something doesn’t come up, it takes forever to even get to one. I sure wish the easy ones are the ones I want… which so far only Arcueid – the rest I don’t really care getting beyond NP1.
…I have a feeling I’ve written something like that before 🤔 I guess it still hasn’t changed.
At any rate, I really should start saving up for whatever coming up next. I need to save at least 330 rolls…
Dead week is dead. Nothing much to do apart of the recollection quests. I don’t think I’ll bother with super recollection quests this time. It’s mainly because it’s quite difficult. The first one is probably not that difficult but the other two are just plain annoying. Constant buff removal just isn’t fun to counter against. For Morgan fight I can probably do quad buff set method (buff main attacker on first turn, swap them out, and swap back in on final break bar) and pray it’s enough to get her down in single turn but yeah 🤷♀️ As for Oberon I don’t even.
The other problem is the reward just isn’t worth shit. And being time limited, I actually forgot to use the LB5 reward last time.
On the other news, I did 66 rolls total for Castoria and got jack shit. At least I did get some SR servants – Nitocris and Zenobia are now both NP3 – but no Castoria. I also got Kaleidoscope (the original) but I need Black Grail more.
There seems to be nothing until at least next week either? ?_? There sure are lots of dead weeks recently. I should probably get around reading the story but too lazy (also I have other things to read).
Finished Tunguska (again) woo. I forgot how difficult the final battle was. Ended up with Ibuki for the first few waves (pretend Koyan above is her) and finished off by solo Tamamo.
Apart of that, the box event is over and I got 100 boxes total. Not quite enough but still helps. In fact I already spent the whole exp cards and QP for getting Arcueid to 120 but she’s still at 115.
Road to 7 LB6 should come up this week. Probably.
Also there’s that Castoria banner. I did 66 rolls and didn’t get her ;_; An NP2 would’ve been nice.
More farming etc. Thankfully I’ve got my Morgan high enough NP and Arash high enough level that it’s possible to farm the last node with full drop bonus CE. Unfortunately it involves a lot of taps though. At any rate, I’m currently at 80 boxes. That’s still quite far away from 100. I still do have hundreds of silver apples though so I’ll see how far I can get this time around.
Meanwhile on challenge quest side, I’m still on lazy mode and holy crap just how far can I push this Morgan/Castoria/Merlin team.
On the sixth challenge, the one with Europe above, the strategy is simple as usual, Morgan deals the damage, Castoria and Merlin provides all the support needed. That said, Europe’s party charm skill is amazingly annoying. At one point she casted it twice in single turn. That should be illegal.
And finally the last one, Morgan v. Morgan. It’s the same team as above. The last few turns I focused mainly on just dealing damage and ended up with this weird situation. I went ahead because she’s got multiple guts and stuff so it actually ended up pretty easy with her solo instead.
The event is ending this week. And it’ll probably be finally time for Road to 7 LB6? Seems a bit late. Also I wonder what will happen to Christmas event this year. They mentioned there won’t be any more new servant this year but Chistmas usually has new servant. The timing also seems rather tight with LB7 release supposedly sometime next month. Not to mention box event usually part of the event would be kind of weird with another box event just ending right before it.
Farming time woo ( ‘_’)>
Also challenge quests. That said, with some stupid team none of them is particularly difficult so far.
First one is single enemy with single target NP Lancer. With some luck and Gudaguda Kanban CE for handling enemy NPs, it didn’t take long. The rest include friend Skadi Summer, Skadi, and Koyanskaya of Light (for NP charge).
Second one I brought the wrong Merlin. Should’ve brought the original Merlin instead for the buster buff. There’s supposed to be Castoria on the third row but she’s gone on the last turn or something.
Third one was almost exactly same team but with correct Merlin. No special strategy here just the usual endurance party but with Morgan instead of Himiko.
And lastly (or at least up to today), yet another of the same but with Melusine instead of Morgan just because she charges NP better and there’s only one target. I didn’t clear up burn debuff before breaking his last bar and thus had to remove about 8 or so guts in the process…
…wait, that was the fifth one. Apparently I forgot to take screenshot of the fourth one. I think it was just Koyanskaya of Light, Arcueid, and Merlin. With my Arcueid being NP5 and all it was almost as easy as the first one.
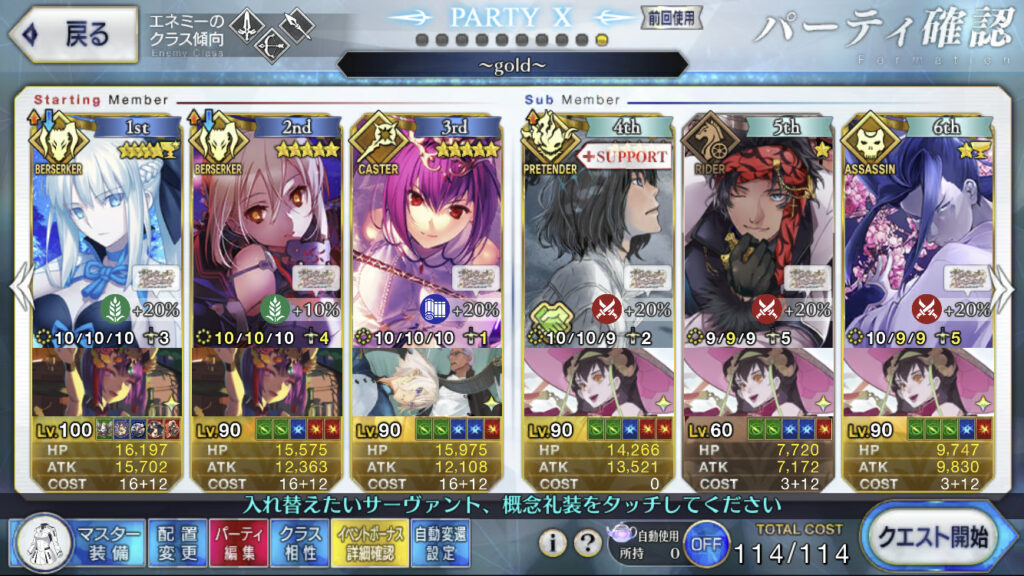
Meanwhile on the farming side, first set’s 90++ was pretty nice and doable with Arcueid. But the second one is a bit annoying for my team. Also I prefer the drop from 90+ so I’m doing that one instead with Ortlinde Summer and double Castoria and Oberon.
Unfortunately the box event didn’t start last week but instead there’s the pre-release event thing 😐
I did the minimum to complete the daily quests by finishing remaining open free quests. There are still quite a few of them. Even once I finish them there are still a bunch of main interludes still need to be completed. I’ll get to them eventually.
In the meantime I’ll be mostly doing the above so I can create the blue apples. Box event coming up next week and I can use a lot of skill stones. I hope I can open at least 200 boxes. Either that or they increase the reward.
On the other news, Morgan banner is up and I did 44 rolls but unfortunately got nothing of use. NP5 Morgan would’ve been useful (currently at NP3). I’ll try scraping whatever free SQ I can get but doubt it’ll mean much.
I forgot to write this multiple times lol.
There just wasn’t anything happening last week. It was all just farming and I’ve cleared the shop.
The rumor says box event may be up next so I’m hoping for that and not going hard on current event farming. I can definitely use some skill stones. Or a lot of them, for all the classes.
There are some new banner reruns but I’m saving for, um, Skadi Summer, I guess, so I didn’t roll. I did exactly two rolls but only got junk as usual.
There are three new Advanced Quests up yesterday but I haven’t looked into it. The annoying part is of course none of the CE so far be limit broken. They’re taking a lot of space now…
Done with the event. Or at least the story and challenge quest. I cleared the challenge quest using that no-fucks-given team above. It’s pretty much just letting Musashi do her NP while Castoria and Proto Merlin being meat shield. I don’t remember exactly how many turns but it was pretty short.
All that’s left for me is farming all the mats and event currencies. Oh and the quest which requires 500 quests completion.
On unrelated note, I forgot to use teapot and thus lost all of them. That sucked.
This event will still be going for two more weeks so there are still plenty of time to farm all the things. Especially void dusts.
I ended up rolling for Koen Shaku except I only got that Kou Hiko above. And Tamamo OG for some reason. That was stupid. I should’ve saved some more. Or a lot more. At least I got to MLB the ☆5 event CE.
As for the event itself, it’s very not Halloween-y so far. The only hint of Halloween is the decorated hall and Eli. No battles are happening inside though and none of the enemies are pumpkin head or other Halloween themed. Oh well =/
The event itself isn’t all that difficult either. Makes one wonder why the requirement of LB5.
The new farming mechanism is mildly interesting though with guaranteed item after certain amount of quests. Thankfully one of the items is void dust which I’m severely lacking at the moment. I don’t know how much I’ll farm but considering QP and embers are also pretty generous here I think I’ll do quite a bit of farming. After the final node is available, of course.
I tried using Sanzo for a bit but it needed quite a lot more care than I could care about. So it’s Tamamo time. In fact she did two of the recollection quests this time around. The class affinity just worked too well.
The Caenis one was done using Morgan/Castoria/Merlin. That one took 37 turns total. There weren’t any weird gimmick so it’s just spamming NP and keeping everyone alive.
I’ve also finished the advanced quests. Some are weirder than the other (the Wolf Game).
On the other news, Halloween is coming up next this week. I’m still trying to save SQ so I don’t think I’ll do any rolls here.
Also, bye NA ( ゚ ヮ゚)a I think I did well overall there. Especially on getting Okita to NP5 and a bunch of other NP2+ servants. Having two years foresight sure is useful.
Road to 7, LB5 edition is here. The recollection quests are absurd as usual. The Corday one is especially annoying with her instant death NP. There’s certainly better method out there but I ended up using one command spell to get MHXA NP charged.
I don’t know if I’ll try them again as I’m currently busy spending all my teapots before they expire in two weeks. The other two were done using the usual Himiko team.
There are also new Advanced Quests. I haven’t looked at them at all…
Christmas rerun is here. Or its pre-release campaign. The actual event is next week. So I’ve been just farming QP.
I’ve got a few more urgent things recently so I may just drop NA sometime soon. It was an interesting experiment but Apple App Store limitation for installing it and inability to purchase SQ directly via Google Play reduced the fun factor quite a lot 🤷♀️
Done with New Yamataikoku. Or at least the quests and stuff. All that remains is farming till drop.
The highest difficulty farming node this time is quite something. I can barely stably farm it with Morgan (NP3), Koyanskaya of Light x2, and Oberon. And the strategy varies based on first turn cards – in the worst case it may take at least three turns. The reward is pretty useful though. I need quite a lot of some of the mats (fangs, fluids, seeds, medals, and hearts).
The challenge quest, as usual as of recently, was done in lazy mode. It’s the usual Himiko, Castoria, and Merlin team. It’s kind of crazy how stable this team is. I did fuck up a bit at the end when aiming for damages to clear the last few bit of first bar. Thankfully the second bar is very easy to clear up. The fuckup was probably even helpful as the enemy steals def buff on bar break and there were none at the time.
As per recent trend, the event will still be up for quite some time. Don’t know how much apples I’ll use here but I still need to save some for actual box event. I need a lot of skill stones of all rarities and classes.
Also finished Yamataikoku here. I didn’t end up farming as much as I wanted partially because of the lack of skill animation speedup and partially the enemies are down quite a lot faster than I wanted. I guess NA is still alive and well.
Cleared the challenge quest with exact same team above lol. I wondered if the class disadvantage matters but it didn’t. Yay.
Unlike JP though there is nothing left to do on the event so I cleared Olympus. Also with the same team above for some of the more difficult quests. I finally cleared the Zeus quest with something other than solo Mash.
The event will be ended next week but there’s no hint of what will come up next. If following JP it would be Christmas rerun…
I still have no idea how the schedule will work out for the remaining of this year.
New Yamataikoku event has started. It’s another one of those box-like event. The closest one I can think of is the Super Bunyan and last year’s summer. The mixture requirement is a bit annoying though. I just hope using them up all won’t involve converting one thing into another.
The story is still ongoing and the presumably best farming node hasn’t appeared so I’m kind of waiting for that. I can use a lot of fangs and medals.
I haven’t tried myself but from what I gather Iyo doesn’t quite refund NP enough for looping. Similar to Ranmaru X maybe?
There isn’t anything particularly interesting banner-wise. I’ve been doing some paid rolls but nothing useful came up so far.
I got the last copy of Okita! Yay. Only took my whole SQ and tickets.
I also got Himiko in 35 rolls. I got her before getting Okita above because getting one of her is quite a bit more important than NP5 Okita.
The raid has started and two of the Nobbu are down. I’ve been slowly going through it with occasional apples but the lack of skill speed up is still a drag after all. I mainly aim to farm enough for all the event currencies.
On another note, during my rolls above for Okita above, at one point I decided I may need to get some additional SQ. So I went through my usual steps of moving the account to Android phone and buy it off Google Play Store. And it didn’t work. I then remembered about buying FGO from wrong region being disabled a few weeks ago. Apparently that applies to me as well so I guess that’s the end of this account’s paid SQ journey. Or maybe the whole account itself because using it on iOS isn’t exactly straightforward due to requiring different Apple ID and all.
I’ll probably continue playing this until I get a different phone or something.
New event is only coming this Wednesday so it’s been just even more farming these last few days. Especially skill stones since I just remembered I ran out of them for some classes (mainly Archer and Caster). I don’t think I’ll get enough of them from just natural AP though.
I did 22 rolls on Amakusa banner hoping for his CE – the one which raises two NP OC levels three times. Unfortunately there’s no such luck. I’ve also been doing paid rolls due to all the extras I got when rolling for Lady Avalon but the only notable result was a single Asvatthaman. An Arjuna Alter would’ve been nice.
It’s farming week here as well and with the last few Hunting Quests being stuff I already have over hundreds of it was just QP and embers and Charlotte.
On the other note, as seen above, I ended up rolling for Okita. I got two of her in 132 rolls. Combined with Illya roll last week I ended up spending over 200 rolls worth of SQ and only have a bit over 100 rolls remaining. I hope those will be enough for Himiko. And I don’t know what will happen next year ( ゚ ヮ゚)a
Yamataikoku here will start on Wednesday which interestingly is the same day as JP’s new Yamataikoku event. The main attraction for this one is of course rolling FP for CE exp cards. With Coin System coming early, it will also double as collecting all the coins. May main concern is of course I don’t have remotely enough space to do it without quckly. At 3.2M FP it’ll take quite a while to use them all.

…what’s in here again 🤔
There’s the 26M DL campaign. 15 tickets bonus is welcome. Can use a lot more lores though. And golden fous.
The updated login bonus is a bit too little of an update but at least it’s something. A bit better than the previous ⭐4 embers.
The new ⭐5 embers in Da Vinci is also welcome. It’s worth the cost now… as long there’s extra mana prism. I don’t know if there’s good justification for the 15 mana prism ⭐4 embers though. Maybe for someone that really has just started? Once one is able to farm the highest diff embers there just isn’t much point collecting the lower rarity ones.
New Advanced Quests have been added. The chain one is mildly amusing with that linked enemies gimmick. It took me a few turns until I realize how to differentiate between servants I have to get rid of and I have to keep alive. I used Castoria, Astraea, and Taisai Seikun.
There isn’t anything particularly special about the Ibaraki Douji one. It’s just defeat the mobs and then the boss while she gets to NP every other turns. It might’ve been a bit easier if I used taunts. But instead I had the same team above except with MHXA Idol instead of Taisai.
Lastly the stake quest. It’s been a while since the last 6 waves quest iirc. I used Arcueid just because it seemed fun. And also Asclepius and Castoria. Nothing special here although I wonder if they actually had Arc in mind with the Avenger enemies.
No info on next event yet so it’ll be another farming week. Both QP and embers… (mainly embers since it’s half AP and I still need a lot for Arc).
Scatfest! And as I remembered the Grail Front AI was hilariously bad. I don’t know what logic they run on as it just seems bizarre with enemy master not running away enough and the servants not hitting master when given chance. The system also pushes for finishing enemy master as soon as possible. They fixed it way later by adding item and challenge nodes. But that’s still a few months away and I think there will be at least one more Grail Front with this stupid arrangement.
Without the skill speed up update it gets pretty annoying farming in NA but I’m still hoping for at least 100 boxes. I’m currently still at 72 boxes so I don’t know if I can actually reach that with 16 hours remaining.
I also did Illya banner and got two of her… ‘_’)a I hope I didn’t mess my chance next year too much. It took me 110 rolls total. I also got two Miyu along the way (now NP3).
There’s also that Fionn thing above. Scath would’ve been nice but I need to save my SQ for next year. Or Himiko at next event. I hope that one won’t take too many rolls. Himiko, combined with Castoria, is kind of crucial for some challenge quests.
That said, the Himiko event itself is still at least one week away with Hunting Quest in between.
Okita banner… I’ll do like 11 rolls maybe. She’ll be back next year anyway.
Pretty just looping the highest diff node ad infinitum. Having to use Order Change is less than ideal but that’s the best I can pull off at the moment.
Also finally got that Lady Avalon above. It wasn’t cheap. I was half expecting seeing myself how pity system works but that didn’t happen. Thankfully.
Along the way I did some paid rolls for all the banners but nothing useful came up so far.
I don’t think there’s anything announced so maybe just nothing for a week? Some kind of main interlude for earlier summer events would be nice.
Scatfest! And it’s last leg already. I haven’t finished the remaining Grail Front but those shouldn’t pose much problem. The AI is still horrible after all. I do look at the guide videos though just so I don’t waste my time figuring out how to do it the most quickly.
As for the farming itself, I’m currently at box 22 but there’s only one extra CE drop so far. I’ll need at least another 3 before I can MLB one. It’s still quite a long trip ahead. The comp for the last one proved to be the most challenging one. Annoyingly I didn’t have the team record from JP but here’s my current comp:
Either first or second turn involves face card attacks. Crit stars are provided by both Saber and Astraea and is pretty stable as either turn should have at least one buster card. There’s a small chance that’s not happening but so far I haven’t encountered that and even in that case Astraea’s arts card can probably provide enough damages regardless.
This will be for another week which then… either a blank week or straight into Himiko. That’ll be my last roll until mid next year. I sure hope black grails will drop by along the way.
And all done! That was quick. I’m feeling lazy so I went with the stupid team for challenge quest (above but with another Castoria as that Merlin was a sub). I should’ve used face card attack for the first turn instead but I think I went with NP. I also made some other misplays like not charging Castoria NP and timed her NP wrong. In the end it’s relatively easy so I still ended up clearing it anyway. May or may not try again sometime later.
As for the rolls, I tried a bit for Skadi and still got nothing. I guess I’ve used all my luck (and SQ) on Arc. At least it’s not like Skadi and Lady Avalon are all that game breaking anyway. It’s nice I don’t need to rely on support Skadi but there’s still not enough buff anyway for quick team to be able to clear farming quests without much restrictions.
I’ll do rolls as SQ comes in but I’m not expecting anything. Also somehow last year summer pick up came in but there’s no rerun. Will there be no rerun of it or what…
Scatfest coming up soon. That was way earlier than I expected. Now I look at the schedule for JP I guess they’re going for slightly more breathing room between events until end of this year.
On the other note, I cleared up all the strengthening and interlude quests. I should get around finishing LB5 sometime. Maybe after Scatfest.
Oh right, I also rolled on the interlude banner. Specifically aiming for Red Hare. And thankfully I got him in first 11 rolls. Two of him to be precise. NP5 would’ve been nice but it’s not like he’s all that useful. No Shuten Douji though.
Next roll will be Himiko. And then I’ll save until next year. I think I’ll skip Muramasa though. I never end up using him much in JP. The main ones next year will be Morgan, Oberon, Koyanskaya Light, and Okita Alter Summer. An NP6 Morgan would be immensely useful.
Summer! New servants! Proto Merlin! (or Merlin’s little sister, Lady Avalon)
I should’ve waited for Skadi Summer details before rolling for her…
Did 134 rolls and didn’t get her. Welp. At least I did get that Faker above which is probably more useful in some ways than Merlin anyway. But it still hurt.
Skadi is coming up next week. There’s no info on her yet so there’s no telling if she’ll be useful at all. Tamamo went from support Caster to being a normal attack Lancer. Whereas Merlin, if we count her/him in, is still support; although the summer version is arguably slightly less useful.
Ibuki Douji is apparently pretty good but she’s a bit too big…
Thankfully this year’s Takeuchi servant is welfare. And it’s Valkyrie. Each of them is being their own thing. It’s been since Mech Eli they did something like this iirc? Though at 3 different servants, I wonder how we’ll be able to get the third one.
Surprisingly DL campaign has already started.
…I don’t know how they’ll fill up the remaining of this year. Also there’s still no skill animation speed up ;_;
As for the event itself, I finally cleared it. It took quite a long time thanks to there being so many nodes.
And then challenge quest, well, I attempted the above. I figured since she’s at NP3 it may surprisingly be possible. And it did. Kind of. The last few turns were scraping all the buff that’s available. Including having Fuuma protect Castoria which very much wasn’t planned.
I then redid with Musashi Summer and it went quite a lot easier. I should’ve prepared Castoria NPs better though.
I sure wonder when they’ll start the Scathach’s Grail Front/Box Event. As this is the very first version of Grail Front, it’ll be hilariously bad as well.

Still anniversary week. The major update after the announcement is of course the daily strengthening quests. There’s surprisingly different types of NP charge this time around. One is just straight out 80% (Jekyll). One is of the usual type 30% (Medusa Lancer). One is of the… weirder type of charging 30% self but also decrease 10% target (Shiki). Which is kind of nice since it means she got what effectively 20% charge when solo and 30% charge when there’s a sacrifice available. And lastly the unexpected one, 10% party charge (Bartholomew, Touta).
The party-wide one is rather nice for some servants since it can round up the missing 10% when having 50% CE + 20% self + 20% append setup.
The new party buffs are nice as well.
Too bad Geronimo still isn’t getting his power up.
On the other hand, as per screenshot above, I ended up with NP5 Arcueid. After the last post, I decided to roll a bit more and she came up again after 43 rolls. Feeling weird, I went all the way with 124 more rolls for her 4th copy, and lastly I decided to go all out and thankfully got her after 91 rolls. RIP my summer. I have a bit over 240 sq and 16 tickets at the moment. I hope those will be enough. Probably not. Oh well.
With that, I also decided to get her to 120. Except I don’t have grail. Or exp cards. Or QP. The last two can be managed somehow but the first one is quite a lot more difficult (or just takes time).
Along the way I also got a bunch of SR servants. Nothing particularly interesting though. And I didn’t get any other SSR.
Next Wednesday will mostly likely be the start of summer event. The rumor has it that there will be 3 new SSR servant this time around. We’ll see.
Ooku has started. It’s a pretty long event in term of missions and nodes. I think I’m almost halfway through it. I just need to make sure to complete it before it’s over (duh).
After that, it should be some kind of DL campaign. No idea if they’ll reach some milestone but I’m still hopeful for the skill animation speed up.
And then it’ll be box event time. With bones and proofs it’s a quite useful one. It’s also the first one which final node drops all shop currencies as well so I just need to do that instead of going through three different nodes to collect them all. I don’t know what comps I’ll use but I’m sure I can conjure up something. At worst it’ll be another plugsuit team.
Anniversary! Summer event sneak peek! Etc.
Well, Proto Merlin Summer is coming up so that’s a thing. There’s Gareth as well with her permanent blush as usual. May or may not skip on either depending on the abilities.
And then there’s GSSR. The main candidates were Archer 1 for all the NP2 possibilities with Moriarty being the only miss. Another copy of Saber Archer would’ve been nice.
And then Archer 2. There’s no real miss there. Orion is sometimes useful. Shounagon, although ultimately useless, is a fun character. And then Jeanne Summer is just plain useful especially with more NP level.
Getting Miss Crane at Caster 2 would’ve been nice but the chance is only 1 in 4. Not to mention it’s got Shikibu which is I’m not really interested in. Now I look again this one isn’t too bad either. NP2 Castoria, while having questionable usefulness, would’ve been nice as well.
In the end Berserker 2 is the only one with full benefit for me. Musashi Summer at NP2 would make her quite a bit more useful as sometimes she just doesn’t deal enough damage. Morgan is no brainer. And lastly Arjuna is still pretty useful although with my current Morgan at NP3 he’s probably just at about the same strength as Morgan. And he is still more powerful in term of face card damage (as long the bonus damage is active).
And the result is Musashi! Yeah, that’s an ok result. Also Brynhildr Summer for the SR is a… bonus. Would’ve preferred Shounagon Summer or Kriemhild. I guess I’ll use Musashi more often now.
Free SSR CE ticket is nice bonus and the current plan is Black Grail. I still need one more afterwards though. It just doesn’t come up…
Oh yeah, there’s that Arcueid banner. Took two tickets to get the first copy. And then another 26 for the second one. That’s an amazing result. NP5 would be interesting but I’m not pushing my luck. Maybe on the last day depending on new summer servants line up.
Almost forgot but Lakshmibai came up along the way. I think I now have all the Takeuchi servants that’s not welfare (still missing Santa Salter and Jailter).
…what’s in here again 🤔
Right, there was this. That was weird. More of her is always welcome though. Just three more until NP6 (ha ha).
Otherwise I’ve been stockpiling QP and clearing up Strengthening Quest backlogs…
Next event, Ooku revival, hasn’t got its date announced. I’d be nice if it’s right after the summer event as there won’t be much in JP for a bit over a week but they probably need a lot of blanks after rushing things for anniversary.
Countdown to anniversary! Summer servant banners! RIP my SQ! Yay.
103 rolls in total before finally getting that Artoria Summer above. Along the way there were Martha Summer (NP2), Kiyohime Summer (NP2), Mordred Summer (NP1), and Astolfo (?, 1 copy for NP5 now). I sure wish I got more than 1 Mordred. I don’t even want the other two which for some reason are both NP2.
At 240 SQ remaining, I hope it’s either nothing interesting on Anniversary and Summer banner or it’s enough to get whatever interesting. It also means no hope of NP5 Okita Alter Summer.
In the meantime, it’s hunting time. The mats so far are all the ones I’m lacking. Considering I’m lacking most of the mats it’s not all that rare of occurrence though. This is also the first time using the bonus drop CEs to their full extent.
Anniversary is coming up in few days and I’m not going to the event! Combination of expensive, far, and covid. And laziness.
Summer event is done-ish apart of clearing the shop and getting one last event CE.
Challenge quest this time is kind of similar to Gilfest MHXA challenge quest in sense one need to get rid mobs first and then finally Bunyan herself. Took two attempts because the first one I let one Castoria dead and the sub members were just whatever.
The plan was probably obvious – it’s just letting Musashi loop her NP ad infinitum with Castoria occasionally providing party-wide invulnerability.
There’s still one more week for the event. I hope it’ll be enough to get the missing CE. Afterwards it’ll be finally Ooku rerun…? Summer passes quickly in NA.
…I still haven’t redone the challenge quest. Oh well.
On the other side, Ooku Main Interlude has been released and along with it Kama rate up banner. I did 11 rolls and somehow she came up at the last one. I already have NP2 Jack so Kama will be mostly useful for clearing up Alter Egos. Although 50% NP charge could still be useful somewhere else.
There’s still nothing announced to fill up the gap until anniversary. Or maybe they’ll have a rerun which just overlaps it? It’s rather unlikely I’d say and it’ll probably be just either complete blank or filler like Hunting Quests.
It’s summer time! Except I’m not rolling or anything so it’s just the usual event!
Also as usual, I’m going slowly through it.
Oh and I did 40 more rolls (30 on Castoria and 10 on Illya) but nothing useful came up. I mean, Waver (now NP2), Stheno (NP2), Valkyrie (NP2), Yan Qing (NP1), and Lancelot (NP1) did come up but I’m not exactly looking for any of them (except maybe Valkyrie). The Waver one was especially annoying because it was on Castoria banner 😐 Where’s Heracles…
Done with the event! Mostly, that is.
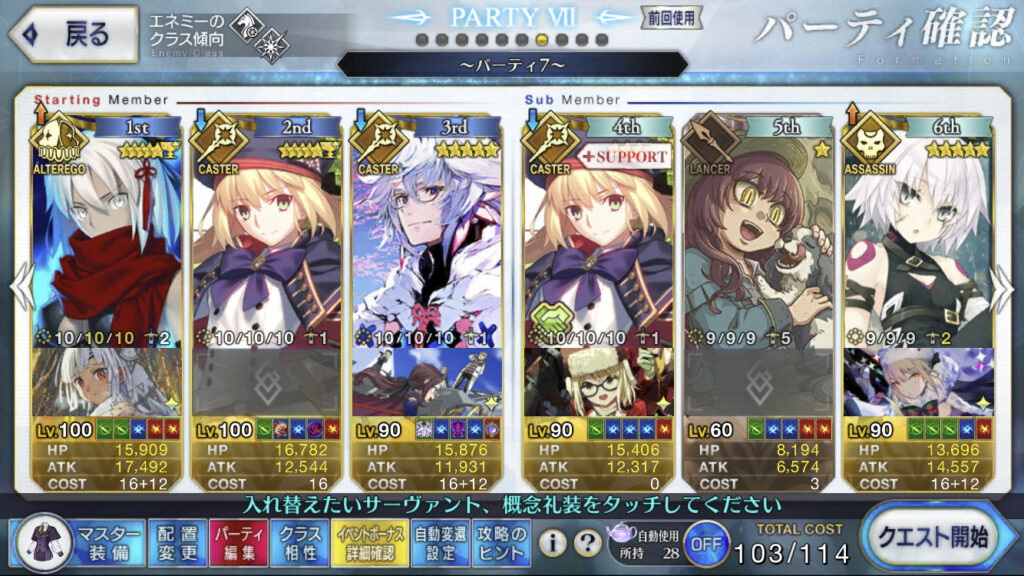
Not the exact team above but I did challenge quest with something like that. Okita Alter cleaning up Hokusai and Bakin as much as possible and then lastly finished off by Jack.
Not a single ounce of elegance. I hope I can get back to it and clear in a more satisfying way.
On the other hand, the event itself will still be ongoing until 20th. With the anniversary event coming up on 30th, it means there will be 10 blank days? Or maybe hunting quest or something like that? Strengthening quests would be nice.
Anniversary! GSSR! Castoria! GSSR was the one above with First Hassan. No Saber Summer so that sucked but at least he could be mildly useful. It’ll be a while until I max him out though because his mats requirement is rather silly.
As for Castoria, thankfully I got her in 77 rolls. It means I still have over 800 sq for future rolls. Unfortunately nothing else useful came up.
Also unfortunately skill speed up animation hasn’t arrived with this update.
Kama event coming up soon. Rolling for NP2 Kama would be useful but I think I’ll save for Himiko and then ultimately next year’s roll fest of Morgan, Oberon, Koyanskaya, and Okita Alter Summer. Those are going to be costly if I don’t prepare early. I especially want some high NP Morgan.
WAIT WHAT they skipped Kama and are going straight to summer? Oh well, that doesn’t change the plan anyway. An Illya would be nice but I really need to save and she’s not all that useful anyway.
An event. Interestingly this time there are two teams running in parallel (although I think the 6.5 was also similar).
Also the expedition thing is kind of interesting? The prize isn’t quite enough though. Auto repeat or something in that order would be useful.
At any rate, it’s business as usual. No rolling this time because neither seem all that interesting.
Anniversary is coming up tomorrow. I should have enough for 300 rolls. I hope that’ll be enough to obtain Castoria.
I’ve also bought enough paid SQ for the GSSR. It’ll probably be second year hoping for Artoria Summer. Complete miss for that year would be Proto Arthur, Moriarty, or Da Vinci. Better-ish result would be Musashi, Ishtar, Tamamo Summer, Illya, or MHXA. The rest are kinda meh but can still be useful.
In the meantime, I’m still farming for mana prism. I need 500 more for the QP/Mystic Code CE and then another 600 for the Fous. There’s also Master/Mystic Code CE coming up but that one is rather useless so I’ll just get one at most.